Version 24.2.0
What's new in this release?
- Display name masking
- To enhance privacy and security, administrators can now mask the VidyoGateway dial-in or dial-out display name.
- The new “dnMask” Advanced Option enables you to mask the caller’s phone numbers so others cannot view them.
- This feature is configurable per prefix.
- To perform the configuration, click the Add Service button on the VidyoGateway Admin UI Services tab. Then, in the Advanced Options field, add dnMask: and the prefix. In the following illustration, entering dnMask:8-* masks the last eight digits of the caller’s phone number.
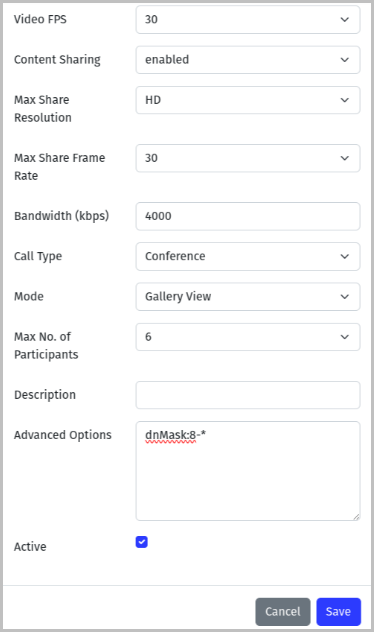
- For example, if the caller’s phone number was +13366666666, dnMask:8-* would create a mask as follows: +13366666666 → +133********
- SSH update and configuration
- This release includes an update to SSH as well as configuration updates to improve security by deprecating legacy protocols.
- Prior to upgrading, please review the SSH configuration information section below in detail to ensure you have the right configuration to connect to the Vidyo appliances after the upgrade.
- Bug fixes
- In this release, we've addressed some issues to improve usability and reliability.
- System updates
- For added security and stability, updates for multiple third-party packages and libraries are included as part of this release.
SSH configuration information
In this version, the SSH configuration has been updated to improve security. Because of these changes, only modern SSH clients that support the configurations below will typically be able to successfully connect.
- Supported host keys: RSA,ED25519
- Key exchange algorithms: diffie-hellman-group-exchange-sha256,diffie-hellman-group18-sha512,diffie-hellman-group16-sha512,curve25519-sha256,sntrup761x25519-sha512@openssh.com,curve25519-sha256@libssh.org
- MACs: hmac-sha2-256-etm@openssh.com,hmac-sha2-512-etm@openssh.com,umac-128-etm@openssh.com
- Encryption ciphers: Ciphers aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-poly1305@openssh.com
Prior to upgrading, we recommend that you:
- Update your SSH client to the latest version.
- Confirm your client supports the above configurations.
- Take a backup (snapshot) of your virtual machine.
- Upgrade a single machine first to confirm connectivity and then proceed to the others.
Upgrade notes
- You must upgrade to VidyoGateway version 24.2.0 from VidyoGateway version 22.2.0 or later. Therefore, if you have a VidyoGateway version earlier than 22.2.0, you must first upgrade to 22.2.0 and then upgrade to version 24.2.0. Please refer to the Upgrade a VidyoGateway 22.2.x cluster to version 24.2.0 section below for more information. These steps must be completed in order.
- If you have installed a previous VidyoGateway version 24.2.0 beta, you should first downgrade your VidyoGateway to a previous GA version using the Recovery Utility on the System Console, and then upgrade directly to the GA 24.2.0 version. For more information, refer to "Run the recovery utility" section of the VidyoGateway Administrator Guide.
Compatibility
VidyoGateway version 24.2.0 is compatible with VidyoPortal version 21.6.x and later.
Files
|
This file... |
Should be applied on top of... |
|---|---|
|
gw-TAG_GW_24_2_0_14-bundle.vidyo |
VidyoGateway version 22.1.0 or later |
Upgrade a VidyoGateway 22.2.x cluster to version 24.2.0
To upgrade a VidyoGateway 22.2.x cluster to version 24.2.0, please perform the following steps in order:
- Place all Cluster Nodes into Maintenance mode.
- Upgrade all the Cluster Nodes.
- When the Cluster Node upgrades are completed and back online, upgrade the current Standby Controller.
- When the Standby Controller upgrade is complete, upgrade the Active Controller. The previous Standby Controller will now become the 24.2.0 Active Controller.
- When the former Active Controller completes its upgrade, it will then become the 24.2.0 Standby Controller.
Resolved issues
The following table lists the issues we resolved in VidyoGateway version 24.2.0.
|
VidyoGateway version 24.2.0 - resolved issues |
|
|---|---|
|
Key |
Summary |
|
VIDGW-5066 |
We fixed an issue where a SIP TLS RE-INVITE occasionally randomly failed due to certificate validation failure. |
|
VIDGW-5065 |
The wrong payload type is no longer inadvertently sent for in-band DTMF to Zoom. |
|
VIDGW-614 |
We fixed an issue where the call process could crash when doing a call transfer via Cisco. |
|
VIDGW-604 |
Apache Tomcat, including CVE-2023-46589, was updated to improve security and stability. |
|
VIDGW-602 |
The Apache web server was updated to improve security and stability. |
|
VIDGW-600 |
OpenSSH, including CVE-2024-6387, was updated to improve security and stability. |
|
VIDGW-522 |
Spring Framework was updated to improve security and stability. |
Known issues
There are no new known issues for this release.